AutoSSL provides a solution to one of the biggest pain points for a website owner: SSL certificate installation and renewal. With AutoSSL that pain goes away. There are no forms to fill out and no certificates to manually copy and paste. With AutoSSL your websites are automatically secured with a free Comodo DV (domain validated) SSL certificate. And at expiration time a new SSL certificate (still completely free) is requested and automatically installed.
What is SSL and why should I care? SSL (secure sockets layer) or TLS (transport layer security) provide encryption and authentication to your website and other services. Until recently SSL was used almost exclusively to secure e-commerce and financial institution sites. But Google, Mozilla, Apple, Microsoft and a few others have decided that the Internet should be more “safe and secure”, and by “safe and secure” they mean encrypted. Without SSL your site will soon become less trusted by the browsers. Visitors to your site will see warnings about security. Without SSL the search engines will rank your site lower. The bottom line. In 2019 and beyond you need an SSL certificate attached to any public facing website or you’ll soon be part of the “grey web”. Maybe a little better than being classified as the “dark web”, but still probably not where you want to be.
It’s nice to have a plan but if Google, Mozilla, Apple, Microsoft wanted everyone to move to an encrypted web they needed to make SSL certificates easy and free. Enter the Linux Foundation. The people who bring you the Linux kernel created a service (LetsEncrypt) that offers free SSL certificates. The certificates are simple DV certificates that expire every 3 months. For most sites a simple DV certificate is all you need to meet the needs of the browsers and search engines. But, LetsEncrypt got off to a bit of a rocky start and the certificates came with limitations we didn’t like.
Comodo, a commercial SSL certificate provider also started a free SSL certificate service. These certificates are also DV authenticated and expire every 3 months but don’t have the same limitations of the LetsEncrypt certificates. Comodo and cPanel, our Hosting Control Panel application, formed a partnership that allows us to provide Comodo backed DV certificates for all your websites hosted with NetGate. And the best part, it’s free and automatic. For each domain attached to your website 3 names will automatically be secured:
your_domain – The base domain name
www.your_domain – The “www” variant
mail.your_domain – The “mail” variant which is often used for mail client configuration
Any subdomains (e.g. blog.your_domain) you add to your site will also be automatically secured by AutoSSL.
If you’re interested in seeing the status of your certificates you can login to your Hosting Control Panel and navigate to “SSL/TLS Status”.
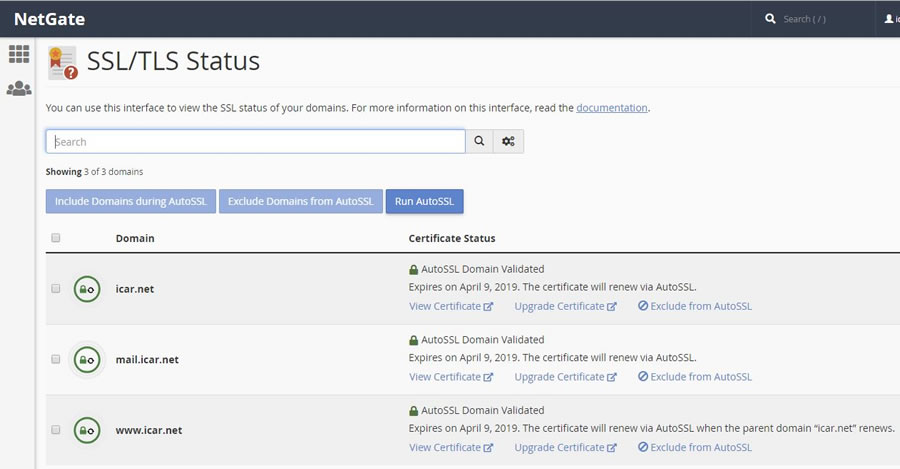
Redirecting all Traffic to your SSL based URL:
Over time the search engines will advertise your secure (https://) based URL but in the meantime you can force visitors to use your secure URL by adding one of the following mod_rewrite rule sets to your Apache .htaccess file. The .htaccess file, if you have one, is located in the document root of your website:
Redirect Method 1
Redirect both the insecure “www” name and the base domain name to the secure base domain name URL.
http://www.your_domain -> https://your_domain
http://your_domain -> https://your_domain
This code redirects both the http://www.your_domain” name and the base domain (http://your_domain) name to https://your_domain.
RewriteEngine On
RewriteCond %{HTTPS} off [OR]
RewriteCond %{HTTP_HOST} ^www\. [NC]
RewriteRule ^ https://your_domain%{REQUEST_URI} [R=301,L,NE]
The first line: Turns on the mod_rewrite engine
The second line: If the request is not using HTTPS
The third line: Or the HTTP_HOST variable is set to “www” [NC means “no case”]
The fourth line: Change “your_domain” to your actual domain name. The rule tells the browser to redirect to your base domain name along with any request URI (e.g. /store/) they may have requested. “R=301” tells the browser this is a permanent redirect, The “L” stops the rewriting process immediately and won’t apply any more rules. And “NE” prevents mod_rewrite from applying hexcode escaping of special characters in the result of the rewrite. This is important for passing some types of data to server correctly.
Redirect Method 2
Redirect both the insecure “www” name and the base domain name to the secure “www” based name URL.
http://www.your_domain -> https://www.your_domain
http://your_domain -> https://www.your_domain
RewriteEngine On
RewriteCond %{HTTPS} off [OR]
RewriteCond %{HTTP_HOST} ^\. [NC]
RewriteRule ^ https://www.your_domain%{REQUEST_URI} [R=301,L,NE]
The first line: Turns on the mod_rewrite engine
The second line: If the request is not using HTTPS
The third line: Or the HTTP_HOST is “www” [NC means “no case”]
The fourth line: Change “your_domain” to your actual domain name. The rule tells the browser to redirect to your “www” name domain name along with any request URI (e.g. /store/) they may have requested. “R=301” tells the browser this is a permanent redirect, The “L” stops the rewriting process immediately and won’t apply any more rules. And “NE” prevents mod_rewrite from applying hexcode escaping of special characters in the result of the rewrite. This is important for passing some types of data to server correctly.
Redirect method 3 (preserve the name used to access the site):
Redirect the insecure “www” name to the secure “www” name.
Redirect the insecure base domain name to the secure base domain.
http://www.your_domain -> https://www.your_domain
http://your_domain -> https://your_domain
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule ^ https://%{HTTP_HOST}%{REQUEST_URI} [R=301,L,NE]
The first line: Turns on the mod_rewrite engine
The second line: If the request is not using HTTPS
The third line: The rule tells the browser to redirect from http to https preserving the hostname along with any request URI (e.g. /store/) they may have requested. “R=301” tells the browser this is a permanent redirect, The “L” stops the rewriting process immediately and won’t apply any more rules. And “NE” prevents mod_rewrite from applying hexcode escaping of special characters in the result of the rewrite. This is important for passing some types of data to server correctly.
The .htaccess File
The .htaccess file that includes the mod_rewrite rules should live in the document root of your website. This is the same directory used for your home page (index.html, index.php, etc.). If the file doesn’t exist you can create it using the method of your choice. For example, you can use a local text editor to create the file and upload it using and ftp application just like you would for any other file used by your website.
If the file does exist:
- Do not duplicate the “RewriteEngine On” line.
- Make sure the lines beginning “RewriteCond” and “RewriteRule” immediately follow the already existing “RewriteEngine” On.
- Make sure you know what you’re doing. You can easily break your website by adding rules to a site already using mod_rewrite.
Your SSL certificate secures your website but is also now used to secure several other services.
Hosting Control Panel Login:
- The URL: http://your_domain/cpanel/ now redirects to https://yourdomain:2087/. Previously it would redirect to a netgate.net based host name.
Mail:
- The hostname “mail.your_domain” should now be used for secure (SSL/TLS) mail client configuration vs. the old netgate.net based name. The old name and associated configuration will continue to work but by switching to the new name for POP and IMAP (inbound mail) your mail configuration will be simpler and the POP and IMAP protocols will use your SSL certificate, instead of the netgate.net certificate, when establishing communications between the server and your mail clients.
- Webmail: The URL http://your_domain/webmail/ now redirects to https://your_domain:2096/. Previously it would redirect to a netgate.net based host name.
FTP:
- The FTP protocol doesn’t support the needed extensions to allow us to attach your SSL certificate to your site. We do secure the server with our own SSL certificate to allow secure FTP communications but as a result your ftp client may still issue a warning when connecting to the server using your domain name. For example, connecting to icar.net using explicit FTP over TLS (Filezilla client) resulted in the following warning:
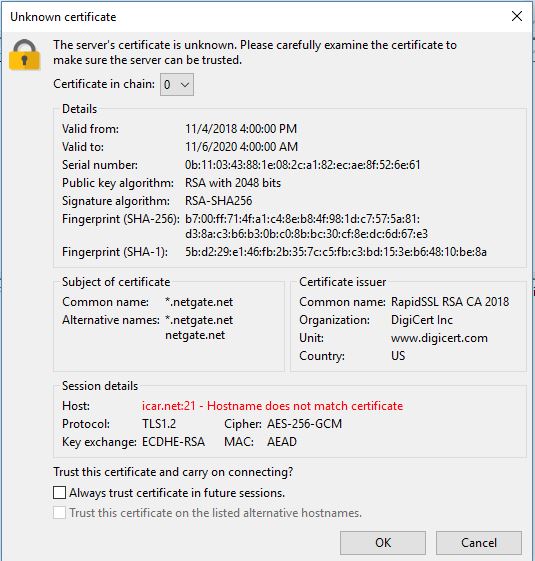
You can safely check the “Always trust certificate in future sessions.” to eliminate the warning.